- This video doorbell camera has just as many features are my Ring - and no subscription required
- LG is giving away free 27-inch gaming monitors, but this is the last day to grab one
- I tested this Eufy security camera and can't go back to grainy night vision
- I replaced my iPhone with a premium dumbphone - here's my verdict after a month
- Build your toolkit with the 10 DIY gadgets every dad should have
COVID-19 Vaccine Themes Persist in Fraud Schemes
Business Email Compromise (BEC)
,
COVID-19
,
Fraud Management & Cybercrime
Fraudsters Impersonate Vaccine Manufacturers, WHO, DHL
Researchers at the security firm Proofpoint are tracking several fraud schemes leveraging COVID-19 vaccine-themed emails.
See Also: The Evolution of Email Security
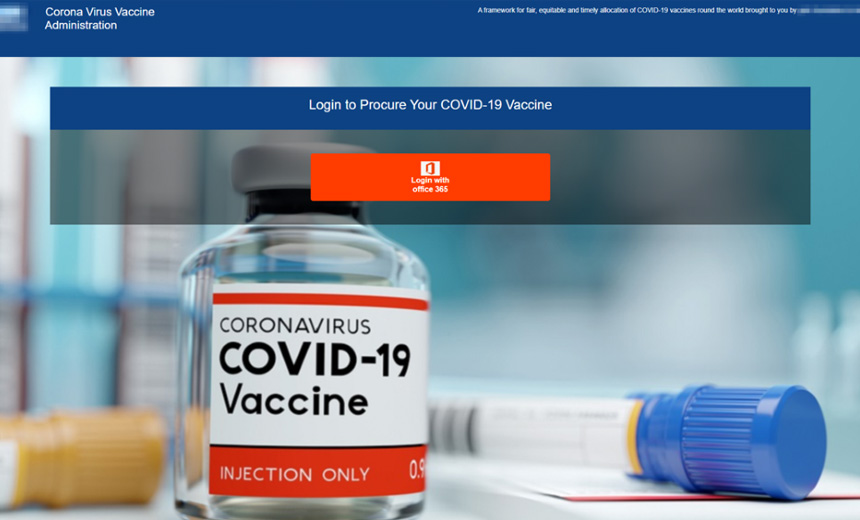
The schemes include business email compromise scams, messages with malicious attachments used to deliver malware and phishing emails designed to harvest credentials – including usernames and passwords for Microsoft Office 365, according to Proofpoint.
The Proofpoint report notes social engineering attacks leveraging vaccine themes have increased over the last two months as pharmaceutical companies have ramped up production (see: COVID-19 Vaccine Documents, Personal Data Leaked).
“Many actors across most geographies are continuing to leverage COVID-19 social engineering, which is an extension of a trend we’ve observed since January 2020,” says Sherrod DeGrippo, senior director of threat research and detection at Proofpoint
Proofpoint found schemes that have spoofed several well-known brands, such as delivery service DHL, as well as vaccine manufacturers in the U.S., Canada, Austria and Germany, according to the report. Other phishing emails are designed to appear as if they originated with the World Health Organization (see: WHO Reports ‘Dramatic’ Increase in Cyberattacks).
“Threat actors are able to change their tactics quickly and align social engineering themes to the news cycle, including the use of stolen branding to give credibility to their attack,” DeGrippos says. “Looking at the news cycle for 2021, possible threat campaigns tied to the new administration’s first 100 days, the gradual reopening of certain industries, and the Tokyo Olympics are potential social engineering themes.”
BEC Scheme
In December 2020, Proofpoint tracked a large-scale BEC scheme that attempted to use COVID-19 vaccine news and rumors of a possible merger or acquisition as a way to target executives, including those with titles such as vice president, general manager and managing director.
“These emails projected that COVID-19 vaccines would fuel the world’s economic recovery,” according to Proofpoint. “The email purported to be from an executive asking the recipient for their cooperation in a confidential acquisition of a foreign company. It claimed that this is an opportune moment to make the acquisition as in the ‘midst of every crisis lies a great opportunity.'”
A smaller BEC scam using similar COVID-19 vaccine messages in emails was also spotted on Jan. 11. Both BEC campaigns potentially could gather information from unsuspecting employees that could be used later to steal company funds, DeGrippo says.
In December 2020, the FBI warned that since the COVID-19 pandemic began, BEC fraudsters have also been attempting to taking advantage of the auto-forwarding feature within compromised email inboxes to trick employees to send them money under the guise of legitimate payments to third parties (see: FBI: BEC Scams Are Using Email Auto-Forwarding ).
Spreading Malware
On Jan. 12, Proofpoint began tracking several hundred phishing emails sent to organizations throughout the U.S. These contained malicious attachments portrayed as containing information about COVID-19 vaccine safety. Some spoofed images and logos from the WHO to add legitimacy.
If victims open the attached document, their devices are compromised by AgentTesla, which acts as a keylogger and information stealer, according to Proofpoint. This malware has become increasing popular with cybercriminals and fraudsters, including gangs running BEC scams (see: Interpol Busts Massive Nigerian BEC Gang).
The Proofpoint researchers report that the threat actor attempting to infect devices with AgentTesla has been using COVID-19 lures since March 2020.
Credential Stealing
Starting on Thursday, Proofpoint began tracking a phishing campaign designed to steal Office 365 and other credentials. These messages, which spoof DHL, target organizations in the U.S., Germany and Austria, according to the report.
The phishing emails, which use DHL logos, urge the potential victims to click a malicious link and to “go online to submit your correct address so we can deliver your package today,” according to the report. If the link is clicked, the victims are taken to a landing page with a DHL logo and asked to input their credentials, which are then harvested by the fraudsters.
“The subject ‘COVID-19 vaccine distribution – Re-confirm your delivery address’ implied to the recipient that the specific package is supposedly a COVID-19 vaccine,” the report states.

